Understanding Segmentation
Network segmentation is a fundamental concept in cybersecurity and network design that involves dividing a computer network into smaller, distinct subnetworks or segments. Each segment acts as a separate network, allowing for granular control over data flow, access, and security policies.
🔑 Key aspects of segmentation include:
- Logical Separation: Segments are typically created using VLANs, subnets, or virtual networks, providing logical boundaries between different parts of the network.
- Access Control: Segmentation allows for the implementation of strict access controls between segments, limiting lateral movement within the network.
- Policy Enforcement: Different security policies can be applied to each segment based on its specific requirements and risk profile.
- Compliance Support: Segmentation helps in meeting various compliance requirements by isolating sensitive data and systems.
- Threat Containment: In the event of a security breach, segmentation limits the potential spread of the threat to other parts of the network.
Implementing effective segmentation requires careful planning and consideration of business needs, data flows, and security requirements. It’s a crucial step in adopting a defense-in-depth strategy and can significantly enhance an organization’s overall security posture.
So, how can we apply segmentation in the network? 🔐
VLAN Segmentation
Virtual Local Area Networks (VLANs) are a common method of implementing network segmentation at Layer 2 of the OSI model. They allow for the logical separation of network traffic within a single physical network infrastructure.
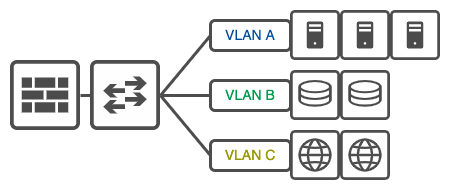
Cons of VLAN Segmentation:
- Limited scalability: Can become complex in large networks.
- Potential for VLAN hopping attacks if not properly configured.
- May not provide sufficient isolation for highly sensitive data.
VLANs serve as a foundational element in network segmentation strategies, offering a balance between security, performance, and manageability. However, they should be complemented with additional security measures for comprehensive protection.
Private VLANs:
Private VLANs (PVLANs) are a Layer 2 security feature that provides isolation between devices in the same VLAN, offering an additional layer of security within a broadcast domain.
Key features of PVLANs:
- Subdivides a primary VLAN into secondary VLANs.
- Typically uses three types of ports: promiscuous, isolated, and community.
- Allows for controlled communication between devices in the same VLAN.
Security benefits:
- Prevents direct communication between end devices in the same subnet.
- Useful for multi-tenant environments or shared infrastructure.
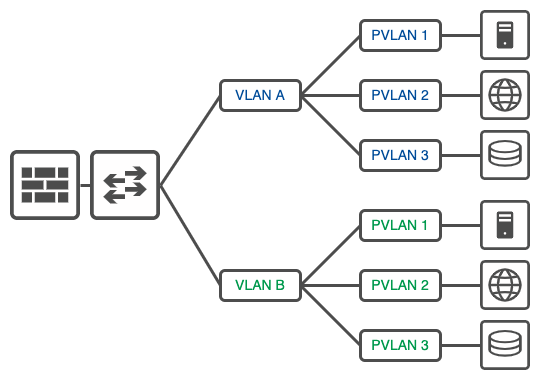
Cons of PVLANs:
- Limited to Layer 2, requiring additional measures for comprehensive security.
- Not all switches support PVLAN features.
- Can add complexity to network design and troubleshooting.
VRF Segmentation
Virtual Routing and Forwarding (VRF) is a technology that allows multiple instances of a routing table to coexist within the same router simultaneously. It provides network segmentation at Layer 3 of the OSI model, offering strong isolation between different network segments.
VRFs are commonly used in enterprise networks and service provider environments to create logically separated routing domains, each with its own independent routing table and forwarding decisions.
Key features of VRF segmentation:
- Provides isolation at the routing level.
- Allows overlapping IP address spaces between different VRFs.
- Supports complex network topologies and multi-tenancy scenarios.
- Can be extended across multiple devices using MPLS or other tunneling technologies.
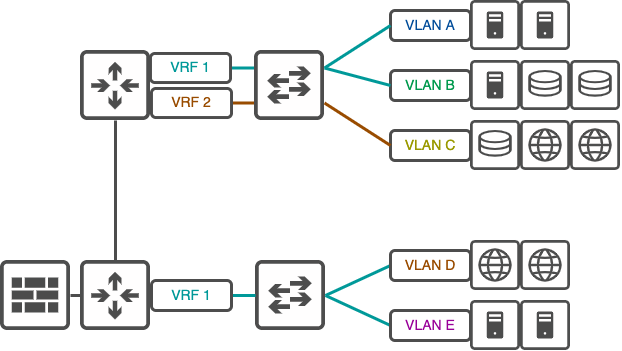
Cons of VRF Segmentation:
- Configuration Complexity: Misconfiguration can lead to security vulnerabilities if routes are inadvertently leaked between VRFs.
- Limited Application-Layer Visibility: VRFs operate at Layer 3, potentially limiting visibility into application-layer threats without additional security measures.
- Potential for VRF Leaks: Improper route distinguisher or route target configurations can result in unintended route leaks between VRFs.
- Incomplete Isolation: While VRFs provide strong routing isolation, they do not inherently provide data plane separation, which may be required for highly sensitive environments.
Micro-Segmentation:
Micro-segmentation is a security technique that enables fine-grained security policies to be applied to individual workloads or even specific applications within a network. It goes beyond traditional network segmentation by focusing on the workload level rather than just network boundaries.
Key aspects of micro-segmentation:
- Provides granular control over east-west traffic within data centers.
- Often software-defined, allowing for dynamic policy adjustments.
- Supports zero-trust security models.
- Can be implemented using various technologies, including SDN, cloud-native solutions, or specialized security platforms.
Security benefits:
- Reduces attack surface by limiting lateral movement.
- Enables application-specific security policies.
- Improves visibility into internal network traffic.
- Facilitates compliance with regulations requiring data isolation.
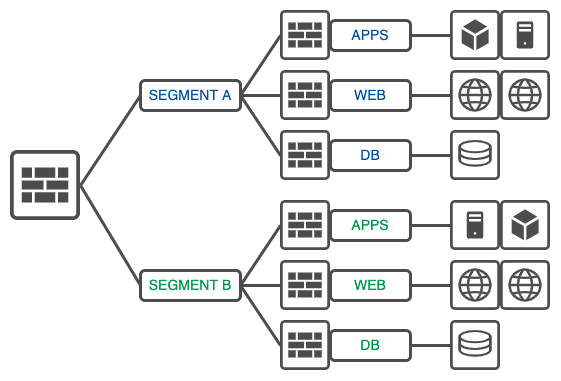
Cons of micro-segmentation:
- Can be complex to implement and manage at scale.
- Requires detailed understanding of application dependencies.
- May introduce performance overhead if not properly optimized.
Zero-Trust Segmentation: Redefining Network Security
Zero-trust segmentation represents a paradigm shift in network security, moving away from traditional perimeter-based models to a more granular, identity-centric approach. This concept combines the principles of zero trust with advanced segmentation techniques to create a more resilient and adaptive security posture.
Key Principles of Zero-Trust Segmentation:
- Trust Nothing, Verify Everything: Every access request is treated as if it originates from an untrusted network.
- Least Privilege Access: Users and systems are granted only the minimum permissions necessary to perform their tasks.
- Microsegmentation: The network is divided into small, isolated segments, often down to the individual workload level.
- Continuous Monitoring and Validation: All traffic is inspected and logged, with real-time policy enforcement.
- Identity-Based Policies: Access is granted based on authenticated identity rather than network location.
Implementation Strategies:
- Software-Defined Perimeter (SDP): Creates dynamic, one-to-one network connections between users and resources.
- Micro-Segmentation Platforms: Utilize software-defined networking to create and enforce granular security policies.
Benefits of Zero-Trust Segmentation:
- Reduced Attack Surface: Limits the potential impact of breaches by containing them to small network segments.
- Improved Visibility: Provides detailed insights into network traffic and user behavior.
- Flexibility and Scalability: Adapts easily to changing network architectures, including cloud and hybrid environments.
- Consistent Security Posture: Applies uniform security policies across diverse IT environments.
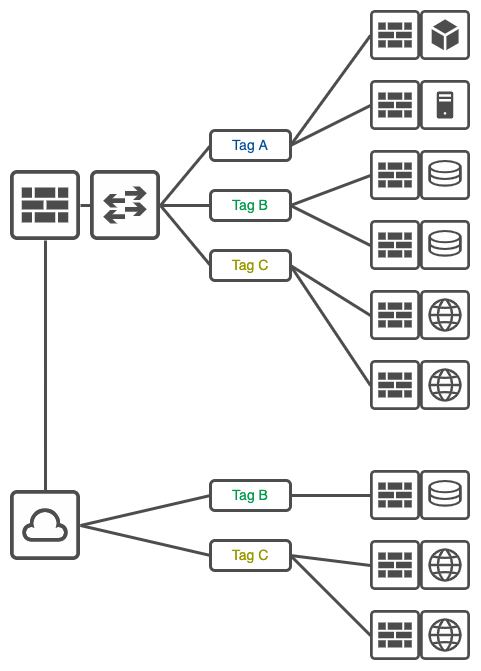
Challenges and Considerations:
- Legacy System Integration: Adapting older systems to work within a zero-trust framework can be challenging.
- User Experience: Balancing strict security controls with user convenience requires thoughtful design.
The Future of Zero-Trust Segmentation:
As organizations continue to adopt cloud services, support remote work, and face increasingly sophisticated cyber threats, zero-trust segmentation is becoming essential.
Future developments are likely to include:
- AI-Driven Policy Management: Utilizing machine learning to dynamically adjust security policies based on behavioral analysis.
- Integration with DevSecOps: Embedding zero-trust principles into the development pipeline for “secure-by-design” applications.
- Extended Zero Trust: Applying zero-trust principles beyond network access to data access and application execution.
Zero-trust segmentation represents a fundamental reimagining of network security, aligning security architectures with the realities of modern, distributed IT environments. While implementation challenges exist, the benefits in terms of improved security posture, adaptability, and breach containment make it a critical consideration for forward-thinking organizations.
